The question of whether or not a VPN provider is able to spy on the traffic of its customers appears to be have been answered this past weekend when one of the favorites in the file-sharing space quite amazingly shot itself in the foot. In a surprise announcement Proxy.sh, a service that has built up a pretty decent reputation, admitted it had chosen to sniff the traffic on one of its United States-based servers in order to catch an alleged hacker.
Our general conclusion was that in the absence of third-party auditing, at the moment it is probably a case of a user assessing a VPN provider??™s attitudes, relying on feedback from existing customers, and then making an educated decision on perceived risks versus potential benefits.
 It appears that the article??™s timing was coincidentally spot on. On Saturday VPN provider Proxy.sh, a company that has built up a decent reputation with good pricing, quality of service and a no-logging policy, made a surprise announcement. It concerned a server the company operates out of Illinois in the United States which had been temporarily shut down and reopened.
It appears that the article??™s timing was coincidentally spot on. On Saturday VPN provider Proxy.sh, a company that has built up a decent reputation with good pricing, quality of service and a no-logging policy, made a surprise announcement. It concerned a server the company operates out of Illinois in the United States which had been temporarily shut down and reopened.???We are unfortunate [sic] to announce that there have been abuse complaints about hacking activities on our U.S. Illinois 1 node. We have been saddened to learn that these actions were harmful to individuals (human beings). As a result, we will open this node again and monitor it with Wireshark for a period of 7 days,??? Proxy.sh announced.
The paragraph requires very little explanation except to underline the fact that a VPN provider has just confessed to spying on customer traffic. Shock of that aside, there was no mention of any legal process, court order, police action or other similar outside influence compelling Proxy.sh to do so.
Bizarrely the VPN provider then went on to give the alleged hacker a public warning.
???If you are the hacker, please stop your activities and leave our network. You are not welcome here. Our heaven is reserved to those who are not harmful to other human beings. If you do not leave, we will find you and report your activities to NGO and press officers,??? Proxy.sh continued.
Then, in an attempt to let other customers know that they shouldn??™t worry, Proxy.sh gave the following assurances.
???For all others, the heaven is still safe for you, dear ones. We will completely remove Wireshark after 7 days and restart the node so that everything is erased (RAM-switch). All other nodes are left unaffected by these actions,??? they conclude.
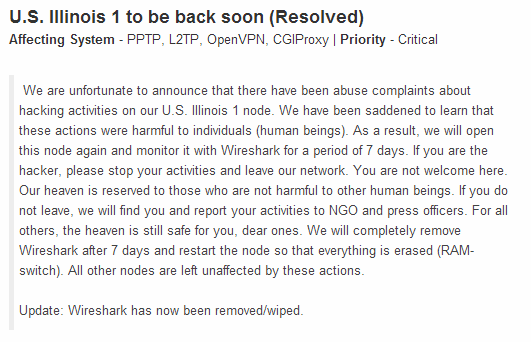
Providing Proxy.sh??™s announcements were roughly around the times that the sniffing software was deployed, the company was capturing packets on its Illinois server between 19:46 on Saturday evening through to Sunday morning at 06:35. At this time the VPN provider posted an update to say that Wireshark had been removed.
A source told TorrentFreak that the monitoring was triggered after Proxy.sh received a complaint from someone who claimed they were being harassed by a Proxy.sh user. The VPN provider then allegedly took it upon themselves to try and sort out the problem. It??™s not clear what happened next but apparently the person responsible for the abuse was either found or stepped forward, prompting an apology and an end to the matter.
While some may argue that Proxy.sh was only trying to act responsibly by ending the abuse and acted properly by giving advance notice to its customers that a server would be monitored, the episode is likely to be damaging to the company.
First of all, the announcement was made , hidden away from easy viewing. Users of the VPN were very unlikely to view the message as the service is accessed through software on their computers. Second, the correct avenue for dealing with these issues is through law enforcement or the courts and the realization that a provider spied on its users (and admitted it) simply because it felt like doing so is quite remarkable.
TorrentFreak approached Proxy.sh for an official statement but we have yet to receive a response.

 Anmelden
Anmelden Benutzerkonto erstellen
Benutzerkonto erstellen










 Nach oben
Nach oben Melden
Melden News
News



 Favoured Toolbase
Favoured Toolbase




